Syft Integration in the Docker Images Plugin
Syft, an open-source scanning tool, is integrated in the Docker Images plugin (starting with the 2022 R4 release). This tool generates a Software Bill of Materials (SBOM) from the discovery of packages and libraries in container images, file systems, archives, and other artifacts. Its integration with the Docker Images plugin enables the plugin to report findings from Docker images containing Alpine, RPM, and Debian Linux distribution packages that reside in RedHat Enterprise Linux, Ubuntu, and CentOS Linux operating systems.
Support for CentOS operating system currently has a known issue in Code Insight in which not all codebase files are being displayed in the Analysis Workbench after a scan.
The following sections provide more information about the integration of Syft in the Docker Images plugin:
Forge Support
The following table shows the supported forges (by package type) for inventory detected by Syft.
| Package | Forge Support for Inventory |
|---|---|
| RPM | Inventory items are associated with components from the following forges: centos fedora gnu fsf github savannah If the component is not found in any of these forges, a custom component is created for the inventory item. |
| Alpine | Inventories are associated with components from the following forges: Alpine centos fedora gnu github If the component is not found in any of these forges, a custom component is created for the inventory item. |
| Debian | Library collection is currently not available for Debian packages. All inventories detected in this package type are associated with a custom component. |
Important Information About the Syft Integration
As you configure and use the Docker Images plugin, keep the following in mind about the Syft integration in the plugin:
Syft as Part of Plugin Bundle
The Syft artifacts are bundled with the Docker Images plugin and are located in the syft directory (directly under the code-insight-docker-images-plugin directory in the Code Insight plugins zip file). Once the zip file is extracted, the syft directory must remain as is along side the code-insight-docker-plugin.jar file. By default, during a scan, Code Insight looks for the syft directory in the same location where this jar file (which runs the scan) is executing. If the syft directory is not found in this location, the scan fails.
The Docker Images plugin uses the 1.9.0 version of Syft.
Inventory Detection Notes
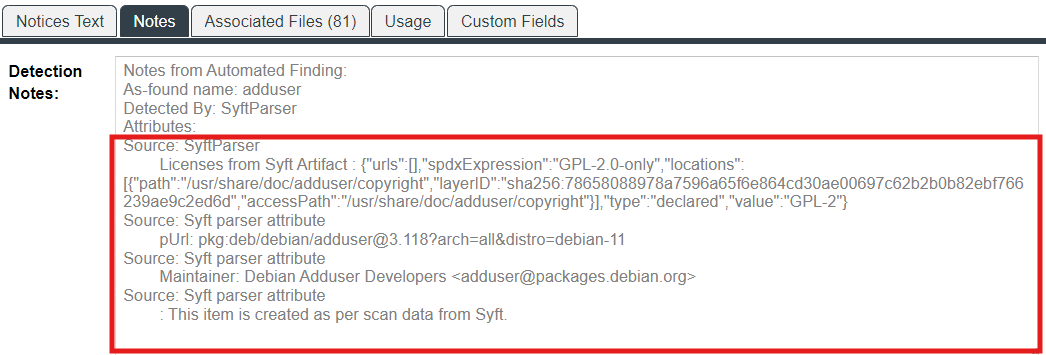
An inventory item discovered by the Syft detection process shows the following system-generated content in the Notes field for the inventory item:
Detected By: SyftParser
Attributes:
Source: Syft parser attribute
This item is created as per scan data from Syft
The Notes field can include other Syft parser attributes as well, as shown in this example:
Inventory Names with Licenses
Only the names of those licenses reported by Syft that have matching names in the Code Insight Data Library are explicitly included in the inventory name. If multiple licenses are reported by Syft, the inventory name can include the names of up to three license matches along with an or more clause, indicating that more licenses (with matches or no matches in the data library) are available for you to review. You can see the names of all matched and non-matched licenses detected by Syft for a given inventory item by accessing the inventory’s Detection Notes in the Code Insight UI.
If Syft reports only licenses that have no matches in the data library (or reports no licenses at all), the inventory name shows Unknown License in its name. You can still see the names of any reported non-matched licenses by reviewing the Detection Notes for the inventory item.
The following table shows examples of how inventory names in Code Insight reflect the licenses reported by Syft for a given component.
| Licenses Reported by Syft | Licenses Matched in Data Library | Example Inventory Name |
|---|---|---|
| "GPL-2", "LGPL-2" | GPL-2.0-only, LGPL-2.0-only | libgcrypt20 1.10.1-2 (GPL-2.0-only or LGPL-2.0-only) |
| "GPL-2", "LGPL-2", "MIT", "Apache-2" | GPL-2.0-only, LGPL-2.0-only, MIT, Apache-2.0 | libgcrypt20 1.10.1-2 (GPL-2.0-only or LGPL-2.0-only or MIT or more) |
| "GP-2", "LL-2" | None | libgcrypt20 1.10.1-2 (Unknown License) |
| "GPL-2", "LL-2" | GPL-2.0-only | libgcrypt20 1.10.1-2 (GPL-2.0-only or more) |
| "GPL-2" | GPL-2.0-only | libgcrypt20 1.10.1-2 (GPL-2.0-only) |
| None | Not applicable | libgcrypt20 1.10.1-2 (Unknown License) |